SSH proxy through remote host using SOCKS v5
I have Tailscale installed on all my machines for remote access to all my machines without leaving any ports open. Great for when I’m out and need to configure my server remotely. However I recently needed to open up ports on my router for a Minecraft server. I could just use Tailscale to let other users connect remotely but at $6 a user a month that would quickly add up.
The Problem
I’m currently out of town. I need to access my router’s web portal and open up one port. This can only be done from a device inside my home network.
The Solution
SSH and SOCKS proxy. I will SSH into a device on my home network using Tailscale and then SSH tunnel all web traffic from my laptop through the device on my home network. It’s really simple! Found this article written in 2009 detailing the exact process. The command is simple.
ssh -D port user@host
Choose a port not in use and connect.
ssh -D 6969 server@tailscale.com
-D as defined in the SSH man page
-D [bind_address:]port
Specifies a local “dynamic” application-level port forwarding.
This works by allocating a socket to listen to port on the local
side, optionally bound to the specified bind_address. Whenever a
connection is made to this port, the connection is forwarded over
the secure channel, and the application protocol is then used to
determine where to connect to from the remote machine. Currently
the SOCKS4 and SOCKS5 protocols are supported, and ssh will act
as a SOCKS server. Only root can forward privileged ports. Dy‐
namic port forwardings can also be specified in the configuration
file.
Finally, edit your network settings. I’m using Pop OS but it should be similar for most distros. Enable manual proxy, fill out the SOCKS field with localhost as the server and the port you chose. Save and you’re done!
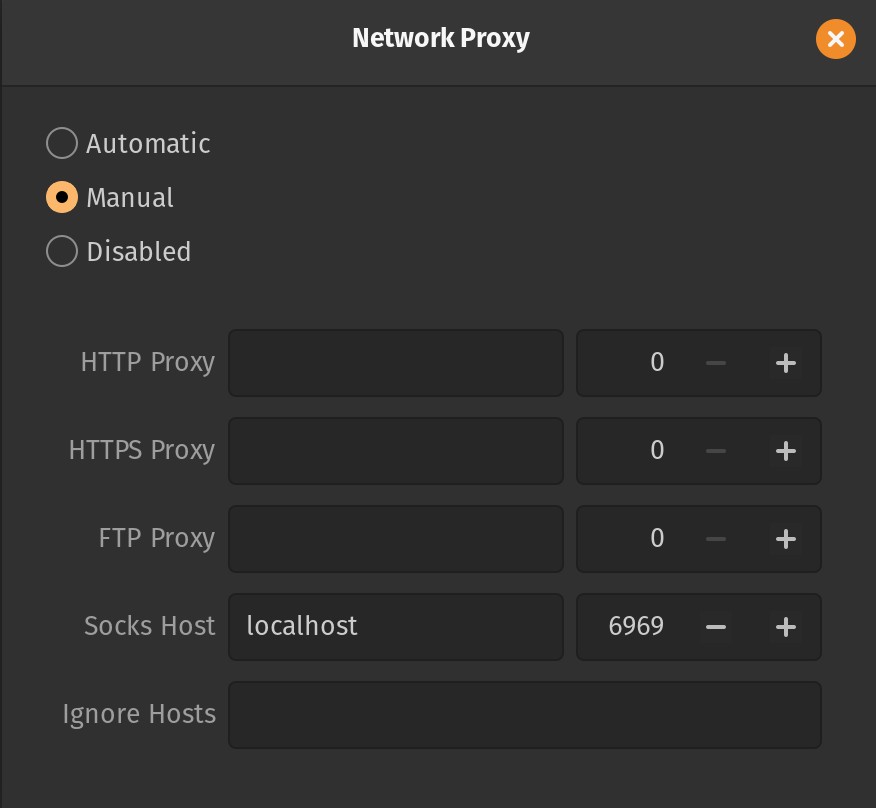
All network traffic should be routing through your device you SSHed into. You can verify this by checking your IP address. From here I connected to the router web portal (usually 192.168.1.1) and was able to login and change settings.